Copyright 2015-2018, Tremolo Security, Inc.
Introduction
What is Unison?
Tremolo Security’s Unison is a unified cloud identity system for web applications. Unison provides the identity functions most commonly needed by applications including:
-
Authentication
-
Federation
-
PIV Cards / SSL
-
Username and Password
-
Virtual Directory
-
Authorization
-
Just-in-Time Provisioning
-
Application Integration
-
User Provisioning Web Services
Unison sits as a reverse proxy between your application and your users:
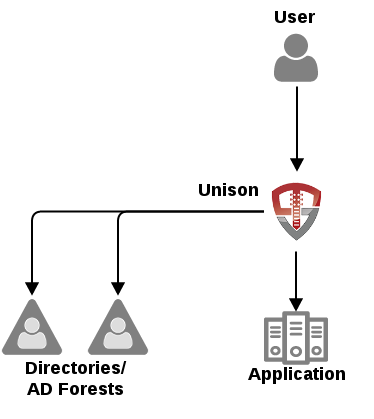
When your application uses Unison users will interact with your application by putting in a url, such as https://www.mycompany.com/application which will take them to Unison. Unison will
-
Authenticate them using its internal LDAP virtual directory
-
Authorize them to use the application
-
Provides mechanisms to be able to add headers and transform the request
-
Forward the request to the application
-
Provide LDAP virtual directory services to the application
-
Process the application’s response
-
Provides mechanisms to be able to add headers, cookies or transform the response
-
Forward the response back to the user
Unison provides a wide variety of functions as a reverse proxy to applications. Applications can leverage Unison as an LDAP virtual directory without using the reverse proxy as in the below diagram:
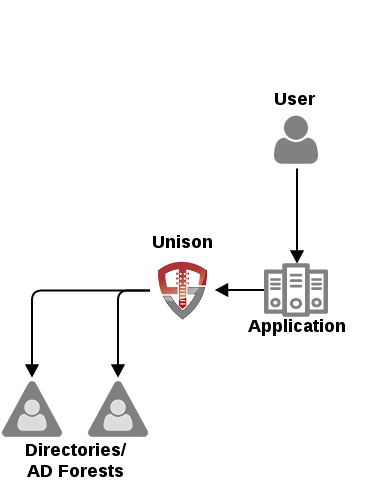
In the above scenario Unison is an LDAP virtual directory that provides identity data to an application using the LDAP standard. This integration method provides a simple integration method for applications that need to authenticate users using a username and password. In this method the sequence of events is:
-
User accesses the application
-
The application prompts the user for a username and password
-
The application uses an LDAP library to search for the user using Unison
-
Unison return’s the user’s Distinguished Name
-
The application uses an LDAP library to perform an LDAP Bind to authenticate the user
Using Unison as an LDAP virtual directory can provide a good first integration step. Note that this method does not provide many of the functionality that Unison offers for applications including:
-
Federation
-
PIV / SSL Authentication
-
Common Access Controls
How Does Unison Integrate with Applications?
Unison provides three primary integration methods:
-
Secure Last Mile
-
Standard Headers
-
LDAP
-
Legacy Provisioning Web Services API
-
RESTful Web Services API
The tightest integration system is Unison’s Secure Last Mile which provides the application identity data in locked down process that minimizes the amount of integration into the application. Additionally Unison can add standard headers to HTTP requests. In addition an application can use standard LDAP calls to Unison to retrieve user data and perform authentication. Finally, Unison offers a RESTful API for retrieving user data and triggering workflows. This API can be used in place of the LDAP Virtual Directory for situations where a web service is more appropriate than an LDAP connection or where user data needs to be updated in a controlled way.
This guide details precisely how to integrate your application with Unison using any of these methods.
What Do You Need to Get Started?
Every application has different requirements for integration. When beginning an integration some items to have are:
-
Application documentation
-
Authentication requirements
-
Identity Data Specs
In addition to identifying how the application will integrate, you will need to work with your Unison administrator to configure Unison and determine how to use the LDAP virtual directory.
Last Mile Integration
Introduction
Unison’s Secure Last Mile is a specialized system that Unison uses to integrate backend applications. The Secure Last Mile system utilizes an encrypted header to secure pass the current user’s context to the application.
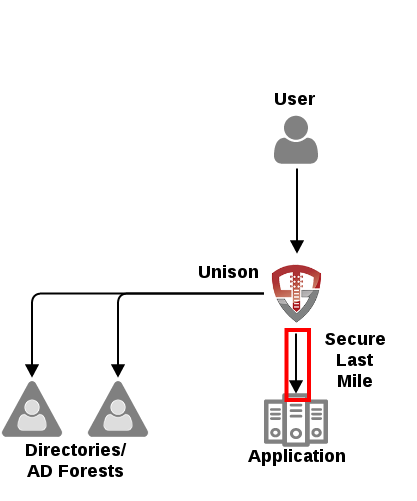
All of the secure last mile systems details below provide identity data in the following ways:
-
User Context – Every web and application server has a custom method for setting the user’s context. For instance in J2EE the context is retrieved using the getUserPrincipal() method. Unison’s Secure Last Mile can create this context.
-
Secure Headers – Many web applications want identity information as a simple HTTP Header in the request. While this method is simple, its insecure as anyone with the correct access can now spoof user information without having credentials to authenticate themselves. Unison solves this problem by providing web applications headers that can be securely relied upon.
-
Role Information – Many web and application servers have the concepts of “roles” to describe how a user has access without having to do a directory lookup. Unison’s Secure Last Mile can provide this information without an extra lookup.
The below sections detail how to use these modules to integrate with your application. See the Unison Installation Guide for instructions on how to install the Secure Last Mile layer for specific systems and the Unison “Cook Book” for specific applications that have been verified to work with Unison.
Java and J2EE
Who Am I?
Java and J2EE provides a basic framework for retrieving identity data for a given user. The Java Secure Last Mile system can:
-
Provide a user principal object
-
Provide role information to satisfy the isUserInRole() method
-
Provide secure headers for attribute information
Unison can provide identity data to a Java application in several ways. Since each application is different, its important to have several options. This section shows, at a code level, how to get the user’s identity using J2EE standards. Note that there are several frameworks for web application development on Java, many with their own ways of getting identity information. You should review your application’s and framework’s documentation for how to extract a user’s identity. Also check out the Tremolo Security Wiki for updates on specific applications and frameworks.
Depending on the J2EE container you can often mix-and-match authentication and data retrieval methods. For instance in RedHat’s JBoss you can configure authentication to use Unison’s Last Mile, but retrieve data using Unison’s integrated LDAP virtual directory. This offers the best of both worlds, as your application can externalize authentication but still utilize the application’s integrated authorization system with virtual data. Check your application server’s documentation and the Tremolo Security Wiki for details on how to perform these types of integrations.
User Principal
Unison supports container managed security by providing the UserPrincipal object that contains the user’s id.
UserPrincipal userPrincipal = request.getUserPrincipal();
String userID = userPrincipal.getName();User Role Check
If an application uses container managed security for checking a user’s role, Unison can map an attribute to a list of roles and make it available to the application:
if (request.isInUserRole(“MyRole”)) {
//Perform an actions
}Secure Header
Many application expect to retrieve the user’s identifier (and other attributes) as headers. Unison’s Last Mile can create these headers without them being transmitted in clear text.
//retrieve the userid from a secure header
String userID = request.getHeader(“USER_ID”);Generic J2EE Servlet Filter
For applications that do not wish to configure container managed security in their application server but want to still use container managed security objects Unison offers a J2EE filter that will wrap the request object overloading the getUserPrincipal(), getRemoteUser() and isUserInRole() methods. It can also create Secure Headers from the Last Mile token.
Unison has filters for both the servlet 2.5 api and the 3.x api. Make sure to choose the api version that is appropriate to your servlet container.
When configuring this filter use the following steps:
-
Ensure that your application server is deployed with unlimited key size for encryption
-
Download the correct Last Mile binaries for your Java version
-
Configure the LastMile Security filter in Unison on your application, place them in the WEB-INF/lib directory of your web application
-
Download the key store from the LastMile Security filter in Unison
-
Add the filter configuration from the LastMile security filter in Unison to your WEB-INF/web.xml file
-
Add the filter mapping configuration from the LastMile Security filter in Unison to your WEB-INF/web.xml file BEFORE any other filter or servlet mappings
-
Deploy your application
While Unison will generate the correct configuration for based on the choices made in the LastMile Security filter configuration, the below table maps out each parameter:
| Option | Description | Example |
|---|---|---|
debug |
If set to true, will output additional log messages |
true/false |
headerName |
Name of the Last Mile header injected by Unison |
tremoloHeader |
roleAttribute |
The attribute from the Last Mile header used to identify roles for the isUserInRole() method |
roles |
createHeaders |
If set to yes the filter will make the attributes configured on the LastMile Security filter available as HTTP headers from request.getHeader() |
yes/no |
userAttribute |
The name of the attribute from the Last Mile header to use to identify the user in the getUserPrincipal() and getRemoteUser() methods |
uid or mail |
keyStore |
The name of the key store relative to the web application’s root |
WEB-INF/lastmile.jks |
keyPass |
The password for unlocking the keystore |
|
encKeyAlias |
The name of the key for decrypting the Last Mile header from the keystore |
|
ignoreURI |
A URI (not relative to the application, but relative to "/") to NOT run verification for. This is useful in situations such as web services that will not go through a Unison proxy and are authenticated using another mechanism. |
/services |
postValidateClassName |
Implementation of the CustomLastMile interface (see the SDK) that can be run AFTER the Last Mile filter has validated the request |
|
verifyOnly |
If set to true the Unison Last Mile filter will only verify the request, but not wrap the request object. This is useful in situations where the application server’s security is used for authentication and setting the user’s context but the Last Mile filter will still be used to verify individual requests. |
false |
Finally, in addition to the standard J2EE apis Unison does provide additional objects not available in the J2EE specs. These objects are proprietary to Tremolo Security and will not exist in other platforms:
| Attribute Location | Name | Description |
|---|---|---|
request |
tremolosecurity.loginlevel |
The numeric value of the authentication level associated with the chain used to authenticate the user |
request |
tremolosecurity.authchain |
The name of the authentication chain used to authenticate the user |
Apache Tomcat Valve
For Apache Tomcat 6,7 and 8 Unison can populate the getUserPrincipal(), getRemoteUser() and isUserInRole() methods using a Valve rather then the generic servlet filter. This offers an advantage of being configured outside of your application’s web.xml file. It can also create Secure Headers from the Last Mile token. NOTE: The valve will execute on every request so there’s no reason to combine this with the generic J2EE filter.
When configuring the valve use the following steps:
-
Ensure that Tomcat is deployed with unlimited key size for encryption
-
Download the correct Last Mile binaries for your Java version
-
Place the binaries in the lib directory of your Tomcat server
-
Configure the LastMile Security filter in Unison on your application
-
Download the key store from the LastMile Security filter in Unison, add it to the WEB-INF folder of your application
-
Add the filter configuration from the LastMile security filter in Unison to your META-INF/context.xml file
-
Deploy your application
|
Note
|
If you change your context.xml it will not be automatically refreshed by Tomcat, you need to delete the old one from the conf directory. |
While Unison will generate the correct configuration for based on the choices made in the LastMile Security filter configuration, the below table maps out each parameter:
| Option | Description | Example |
|---|---|---|
debug |
If set to true, will output additional log messages |
true/false |
headerName |
Name of the Last Mile header injected by Unison |
tremoloHeader |
roleAttribute |
The attribute from the Last Mile header used to identify roles for the isUserInRole() method |
roles |
createHeaders |
If set to true the valve will make the attributes configured on the LastMile Security filter available as HTTP headers from request.getHeader() |
true/false |
userAttribute |
The name of the attribute from the Last Mile header to use to identify the user in the getUserPrincipal() and getRemoteUser() methods |
uid or mail |
pathToKeyStore |
The name of the key store relative to the web application’s root |
WEB-INF/lastmile.jks |
keyPass |
The password for unlocking the keystore |
|
encryptionKeyName |
The name of the key for decrypting the Last Mile header from the keystore |
|
ignoreURI |
A URI (not relative to the application, but relative to "/") to NOT run verification for. This is useful in situations such as web services that will not go through a Unison proxy and are authenticated using another mechanism. |
/services |
postValidateClassName |
Implementation of the CustomLastMile interface (see the SDK) that can be run AFTER the Last Mile valve has validated the request |
Finally, in addition to the standard J2EE apis Unison does provide additional objects not available in the J2EE specs. These objects are proprietary to Tremolo Security and will not exist in other platforms:
| Attribute Location | Name | Description |
|---|---|---|
request |
tremolosecurity.loginlevel |
The numeric value of the authentication level associated with the chain used to authenticate the user |
request |
tremolosecurity.authchain |
The name of the authentication chain used to authenticate the user |
Oracle Weblogic
Oracle Weblogic supports Identity Asserters which may be used to set an application’s identity inside of Weblogic (as opposed to just in the application). This is useful in situations where an application is relying on web services, queues and other container managed services. Finally, when using Fusion Middleware stack this identity asserter will provide the proper information.
|
Note
|
When configuring the Identity Asserter Last Mile will ONLY run when authenticating a user. If Unison is being used for authorizations it is recommended that the LastMile J2EE Filter be deployed verifyOnly=yes to continue to enforce authorizations. |
When configuring the Identity Asserter use the following steps:
-
Ensure that Weblogic is deployed with unlimited key size for encryption
-
Download the correct Identity Asserter for your version of WebLogic
-
Place trmeoloIdentityAsserter.jar in $WEBLOGIC_HOME/wlserver_10.3/server/lib/mbeantypes
-
Place the additional jar files in $WEBLOGIC_HOME/wlserver_10.3/server/lib
-
Configure the LastMile Security filter in Unison on your application, ensure that the header name is "tremoloHeader"
-
Download the key store from the LastMile Security filter in Unison, place it in a location that is accessible by Weblogic
-
Restart the Weblogic administration server
-
From inside of the Weblogic administation server, add a TremoloIdentityAsserter provider and set it to the top of the list
-
Configure based on the below table
Weblogic Identity Asserter Configuration Parameters:
| Option | Description | Example |
|---|---|---|
Debug |
If set to true, will output additional log messages |
true/false |
UserAttribute |
The name of the attribute from the Last Mile header to use to identify the user in the getUserPrincipal() and getRemoteUser() methods |
uid or mail |
KeyStorePath |
The full path to the Java keystore generated by Unison |
/home/oracle/lastmile.jks |
KeystorePass |
The password for unlocking the keystore |
|
KeyAlias |
The name of the key for decrypting the Last Mile header from the keystore |
|
PostValidationClass |
Implementation of the CustomLastMile interface (see the SDK) that can be run AFTER the Last Mile valve has validated the request |
Microsoft IIS
IIS is supported for ASP.NET 4.x and up, as well as legacy applications configured using the integrated pipeline.
Who Am I?
Unison can provide IIS and ASP.NET based applications a wide array of identity integration options. The ASP.NET Secure Last Mile layer is a standard .NET IHttpModule that transparently decodes the Secure Last Mile header and provides your application identity data.
Impersonation
IIS is often deployed with Active Directory to support users. This offers the advantage of using AD as a single point of management for identity information. Unison can integrate with applications using Microsoft’s extensions to Kerberos called S4U2Self and S4U2Proxy, also known as Constrained Delegation and impersonation. This allows applications that rely on Kerberos tokens and authorizations in AD groups to continue to use them. When using impersonation, the user’s identity can be taken for the typical Windows Identity Foundation objects.
IPrincipal Object
To retrieve a user’s IPrincipal object:
System.Security.Principal.IPrincipal user = Context.User;
String loginID = user.Identity.Name;Role Check
To check a user’s roles:
System.Security.Principal.IPrincipal
user = Context.User;
if (user.IsInRole("MyRole")) {
//do something
}Injection
If Active Directory is not being used for web applications Unison supports injection in a similar fashion as with J2EE and LAMP applications. Using injection the Windows Identity Framework objects are still available, but an application can also leverage Secure Headers.
IPrincipal Object
To retrieve a user’s IPrincipal object:
System.Security.Principal.IPrincipal user = Context.User;
String loginID = user.Identity.Name;Role Check
To check a user’s roles:
System.Security.Principal.IPrincipal
user = Context.User;
if (user.IsInRole("MyRole")) {
//do something
}Secure Headers
Unison can create headers which are encrypted transparently to the application and can be retrieved using standard ASP.NET code for retrieving headers:
Request.Headers.GetValues(“USER_ID”);ASP.NET IHttpModule
The ASP.NET IHttpModule for IIS provides the bridge from Unison to IIS. It will support either an ASP.NET application running in a classic pipeline or a legacy application running an integrated pipeline. To deploy the module:
-
Copy the TremoloLastMileDotNet.dll into the application’s bin directory OR install into c:\Windows\Assemblys
-
Create a Last Mile Security filter in Unison
-
Add the "appSettings" section of the Last Mile configuration to the "configuration" section of the Web.config file
-
Add the Last Mile module to the configuration.system.webServer.modules section of Web.config
The following configuration options are available for the IHttpModule:
| Option | Description | Example |
|---|---|---|
headerName |
The name of the Last Mile header |
tremoloHeader |
key |
Base 64 encoded key used to decrypt the Last Mile header |
|
createHeaders |
If true, the attributes configured in the Last Mile header are added as headers to the request |
true/false |
validate |
If true will validate that the Last Mile header is for the correct URI and in the correct time span |
true/false |
createUser |
If true, will create a Windows Identity Foundation object for the user |
true/false |
impersonate |
If true will create the Windows Identity Foundation object via impersonation (S4U2Self & S4U2Proxy) |
true/false |
upnAttributeName |
The name of the attribute from the Lat Mile header that represents the user’s login id |
rue/false |
Apache
The Apache HTTPD server is supported using an authentication module that works similarly to mod_auth_ldap or any other authentication module in Apache. This module is stateless and does not maintain a session however it will, on each request, either create headers or set the HTTP_REMOTE_USER environment variable.
Who Am I?
Each language that runs on Apache (ie PHP, PERL, Python, Ruby, etc..) has its own methods for extracting a user id from Apache (or a header). See each platform’s documentation for how to extract the user’s identity based on the HTTP_REMOTE_USER environment variable or a header created by a Secure Header.
mod_auth_tremolo
The mod_auth_tremolo Apache module requires:
-
httpd
-
openssl
-
boost-date
The steps for deploying mod_auth_tremolo are:
-
Copy mod_auth_tremolo.so to the Apache modules directory
-
Add "LoadModule auth_tremolo_module modules/mod_auth_tremolo.so" to the httpd.conf file
-
Inside of the context that the Last Mile module will have context, add the configuration for mod_auth_tremolo
The following configuration options are available for mod_auth_tremolo:
| Option | Description | Example |
|---|---|---|
AuthType |
Apache configuration to specify how a user is authenticated |
TremoloLastMile |
TremoloHeaderName |
The name of the Last Mile header |
tremoloHeader |
TremoloEncodedKey |
Base 64 encoded key used to decrypt the Last Mile header |
|
TremoloCreateHeaders |
If On, the attributes configured in the Last Mile header are added as headers to the request |
On/Off |
TremoloUidAttributeName |
The name of the attribute from the Lat Mile header that represents the user’s login id |
uid |
Require |
Apache configuration option to specify who is authorized |
valid-user |
IdP Initiated SAML2
Some applications will not easily accept a header or other means to externalize the authentication of a user, but they will accept a SAML2 token using IdP initiated assertions. To configure this method, see the Pre-Authentication HTTP Filter configuration in the Unison Administration Reference Guide for details on how to configure this option.
Who Am I?
See the application’s documentation on how to integrate.
Generic Headers
In the event that an application can not support a Last Mile configuration Unison is capable of creating generic HTTP headers using a Result Group that will be configured on the application. This method is the least secure of all methods as these headers can easily be spoofed by bypassing Unison. To protect against this scenario it is recommended that HTTPS Mutual Authentication is configured between Unison and the application’s web server.
Who Am I?
See the application’s documentation for how to extract injected HTTP headers.
LDAP Virtual Directory
Introduction
Unison utilizes an internal virtual directory for accessing user data. This directory can use LDAP directories, Active Directory forests, relational databases and even custom stores like web services. Unison’s virtual directory supports only the search and bind LDAP operations. Entry modification and addition are not supported via the LDAP interface. To update data, it’s suggested that you integrate with the workflow engine covered in this guide.
Schema Normalization
An LDAP virtual directory often combines disparate directory sources, such as an Active Directory and a standard inetOrgPerson directory such as Sun Directory and a relational database. To combine these sources into a usable format Unison must normalize the attributes into a common format. The format Unison uses is the inetOrgPerson LDAP schema. The below table has common attributes and how they map in Unison.
| Use | Active Directory | inetOrgPerson | Unison |
|---|---|---|---|
User Name / Identifier |
samAccountName |
uid |
uid |
Group Membership |
member |
uniqueMember |
uniqueMember |
This means that if the directory that stores your users is Active Directory, but you are accessing it via the Unison virtual directory you would search for the user using the attribute “uid” rather than the Active Directory attribute “samAccountName”.
Data Organization

Data is organized in a standard form in Unison’s Directory Information Tree (DIT). All user data is stored under “o=Tremolo” with each configured directory as an ou underneath with the name as configured in Unison. For instance if three directories are configured : “Internal Users”, “External Users” and “Contractors” the following DIT would exist:
Interacting with Unison’s Virtual Directory
How to Authenticate Users
User authentication in LDAP is generally a two-step process:
-
Search for the user using whatever username they provided (ie a user id, email address, etc)
-
The search results will return an entry with a distinguished name; use the Distinguished Name in an LDAP Bind operation to authenticate the user
When searching for the user always use the search base of “o=Tremolo” as described in “Data Organization”.
How to Retrieve User Data
User data is retrieved from Unison’s virtual directory using the standard LDAP search operation. As explained in the previous sections, the root of the virtual directory is “o=Tremolo”.
Connection Management
When interacting with a virtual directory there are typically two models:
-
Single Pool – A single pool of connections is used with a single service account. This model is most often used when only retrieving user data from the virtual directory.
-
Dual Pool – Two pools are utilized. The first is referred to as a “Search” pool and is used for looking up user data. This pool uses a single service account like the pool in the “Single Pool” model. The second pool is used for LDAP Bind operations to authenticate users. This pool is only used for authentication so no service account is used.
For security and performance reasons option =2 is recommended when performing authentications. While a single pool could be used it would require a rebind on every search operation or complex logic for tracking which account the current connection is bound to often injecting security risks.
ScaleJS Provisioning API
Each of the ScaleJS applications has a RESTful API that can be interacted with from your own applications. There are no specific authentication requirements for each application, only what you choose to configure in Unison. Any authentication chain or mechanism will work with these APIs. All requests are made in the scope of the currently logged in user.
ScaleJS Main
The main ScaleJS application has the majority of the APIs with functions to request workflows to be executed, update the logged in user, execute approvals and view reports.
All URLs assume that scale’s filter is deployed to /scale/main.
Get Configuration
Purpose |
Retrieves the configuration for ScaleJS |
URI |
/scale/main/config |
Method |
Get |
{
"displayNameAttribute": "displayName",
"uidAttributeName": "uid",
"frontPage": {
"title": "Azure Cloud Linux Management",
"text": "Use this portal as the gateway for accessing your linux servers and requesting access to systems."
},
"canEditUser": true,
"showPortalOrgs": false,
"logoutURL": "\/logout",
"attributes": {
"ipaSshPubKey": {
"name": "ipaSshPubKey",
"displayName": "SSH Public Key",
"readOnly": false,
"required": true,
"minChars": 0,
"maxChars": 0
},
"uid": {
"name": "uid",
"displayName": "Login ID",
"readOnly": true,
"required": false,
"minChars": 0,
"maxChars": 0
},
"loginShell": {
"name": "loginShell",
"displayName": "Login Shell",
"readOnly": false,
"required": true,
"minChars": 0,
"maxChars": 0
},
"displayName": {
"name": "displayName",
"displayName": "Display Name",
"readOnly": true,
"required": false,
"minChars": 0,
"maxChars": 0
},
"givenName": {
"name": "givenName",
"displayName": "First Name",
"readOnly": true,
"required": false,
"minChars": 0,
"maxChars": 0
},
"sn": {
"name": "sn",
"displayName": "Last Name",
"readOnly": true,
"required": false,
"minChars": 0,
"maxChars": 0
}
},
"roleAttribute": ""
}Get User
Purpose |
Retrieves the configured user attributes for the logged in user |
URI |
/scale/main/user |
Method |
Get |
{
"uid": "mmosley",
"dn": "uid=mmosley,cn=users,ou=azure.cloud,o=Tremolo",
"attributes": [
{
"values": [
"ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDTcmV5wGw6KDIAp0HiFh7VRESjAdPKpomGelOQC+Z\/2E5K+l6tfU3NOz6HXsyBreqx60ngEdRoN0u9lBToDpIyMchF6rQFYup8sECIZOEM5rm+qdwHD6UE1vogp9suNO9MNNpCXPAIK5wNJQS8BpHCX+bqHWjIdWB6OqmjQwCfvCQ5fgfAE9oTVrDCtS4Vv8NdkHcy8JIUH+I+02misDlXXURxksE12dl1MhKG4ZQrRJ3LH4c5ox2af\/\/N5q5QC3pmd0AgXWO1DdUfr0mzv2EW8G6ArCqhnjcs7zgJPLWhM+NW0NG5i29a2IlXP9Qzgg7\/shgqDRDxlYFue7x0Po2P mlb@Marcs-MBP.home"
],
"name": "ipaSshPubKey"
},
{
"values": [
"mmosley"
],
"name": "uid"
},
{
"values": [
"\/bin\/bash"
],
"name": "loginShell"
},
{
"values": [
"Matthew Mosley"
],
"name": "displayName"
},
{
"values": [
"Matt"
],
"name": "givenName"
},
{
"values": [
"Mosley"
],
"name": "sn"
}
],
"groups": [
"admins",
"ipausers",
"sudoalls",
"admin-approvers",
"graylog-administrator"
]
}Get Organizations
Purpose |
Retrieves the organizations authorized for the logged in user |
URI |
/scale/main/orgs |
Method |
Get |
{
"id": "687da09f-8ec1-48ac-b035-f2f182b9bd1e",
"name": "MyOrg",
"description": "MyOrg Azure Cloud",
"subOrgs": [
{
"id": "e6b5b365-9dc4-47f4-803f-a1255cf31b57",
"name": "Administrator Access",
"description": "Various administrative roles",
"subOrgs": [
]
},
{
"id": "5d6bab30-9dd9-4cfd-8aff-a395fed377dc",
"name": "Log Management",
"description": "Log management roles",
"subOrgs": [
]
},
{
"id": "1c2cad5b-f62c-491c-84f3-068f6231f053",
"name": "Identity Management Reports",
"description": "Reports Available to Identity Management Admins",
"subOrgs": [
]
}
]
}Get Workflows
Purpose |
Retrieves the workflows for a given organizations id |
URI |
/scale/main/workflows/org/ORGID where ORGID is the organization’s ID |
Method |
Get |
[
{
"name": "request-graylog-reader",
"description": "View log data",
"label": "Graylog Read Only"
},
{
"name": "request-graylog-admin",
"description": "Manage & Configure Graylog",
"label": "Graylog Administrator"
},
{
"name": "request-demogroup",
"description": "Demo Things",
"label": "Demo Group"
}
]Check if User Can Pre-Approve or Request for others
Purpose |
Check to see if the current user can either request for others or can attempt a pre-approval. |
URI |
/scale/main/workflows/candelegate?workflowName=WORKFLOW_NAME&uuid=XXX-XXX-XXX-XXX where WORKFLOW_NAME is the name of the workflow to check and an optional uuid to identify the request |
Method |
Get |
{
"canDelegate":true,
"canPreApprove":true,
"uuid":"xxx-xxx-xxx-xxx-xxx"
}Execute Workflows
Purpose |
Execute a set of workflows as the user |
URI |
/scale/main/workflows |
Method |
Put |
[
//Example of a request that is pre-approved for testsamlx by the current user
{
"reason":"test",
"approved":true,
"subjects":[
"testsamlx"
],
"name":"testDynamicApproval",
"doPreApproval":"true",
"approvalReason":"testing",
"encryptedParams":"eyJpdiI6IktEbzFVeUxyeVNhTnBHM29TZkNuTlFcdTAwM2RcdTAwM2QiLCJlbmNyeXB0ZWRSZXF1ZXN0IjoianBzTUU3Uk4wVytFajhwNTJzRzFJWmNxOU92SHRDWjB3cUFNSE1UeTVQVkJtS2JJWkdpOUlXd0s1OE96Z0dXWlhPMktuSWtWWk43WlJ0MHJmVGh3aStvNzhGZE5vZGRrUjN4VHB5RjVaQ1NHQW1BbDlMZE8yNWVkOFZtMXFlZzJvRXJJMWdKMGdsRDVvUE8xU05Xb0RnM1VSV29oeDlIZzBRcmthQ0U3b3JMbzdkTTkweW83Q3oyelJZVUc4VU1hclNNSEg4VjVQanpTTWRDdy82dE93RXRscEhsUzA1cUlSNkNyZVZtTE1iaUV5QmpzTXdjSGloam4zcmlDUE5NL05icTE5VFd3emM0VmwwV0t6WlJwNUxkNTYxaWtWb1lQcW5LTEp0aU5jc3E0NTdrZnBMV3E5RUhDc2VpUDUzTVlURXZqKzdVSzVzWEpXNk00NkdxTisxa2dtSUIwNytva3VBcWp6MzBSODFpZWI4MGtXUkpkZldFNysvYStIcW1uNHJFMU1IbGxGR3NaekdXRElzeGRvcU4weURpZkhwNFhZSnU2U203ZkYxWlFyVlNZd2N6VDVqbUNYbEtaZndSQSJ9",
"uuid":"6d1c9443-fa37-46e3-83c9-0901451ed633"
},
//Example of a request for another user, but NOT pre-approved
{
"reason":"test",
"subjects":[
"testsamlx"
],
"name":"testDynamicApproval",
"doPreApproval":"false",
"encryptedParams":"eyJpdiI6ImEwdllIK0RjZ3VZbWg0N2o1ZnltcFFcdTAwM2RcdTAwM2QiLCJlbmNyeXB0ZWRSZXF1ZXN0IjoiOVZsRHd2aU9ucHUvZlFzMW1sMzZWUHM3OXVFZTZQU0k0Z2FIaEl0dkJEeWJBVnZLUW1OOVFVV3JoVXdZZTkwOFJKSDU2cHpvTTN0ZHFsRkpja2l5MEdUNTVCMVo5UUJxQzZBZHZTM2x0QWtOZWxhMmtlbEtubHJ5WXVuYmNqaEhML2ROV1R6ZThQR25ndWEwaWM1OERFdG1SdVNOOHBHbG90aFcrVUkySnBveVNCK2NBVGRmWW1EbS9JeDg1cmgzcVF0ekFnRHRkYUxvRHEvQzJOb25EaS9JMjJXdnphblZYRlFJWjFLNUEvd3I5eGhBVmpVbk5KOGhSSC8zajd2QXVmSkQ5OXJGQnd1RDduWXB4ZkZvZFh2bXlpcmhKSTZzcnRQY2FLRHpYZlh2KzV3ZkpNY3o1eUhiQWoyTFlEV2xkaUl4c3dlMUljSDhjTHdpbDMyR2wxaG1pWDlLL01LeUFBTUVJR0JUTFhhM25uTXJoaFZ0MkY4bC9ZKzZRK1lOcDBWVGQwUlBnVWVIZzdqOGJ3aU1MMVFETm5RQkQwMldNVXQvTEcyMVR6L2VQYWtvc3ZuenFZaHJhZVp6dHV0eiJ9",
"uuid":"1f5bd4e6-9525-4c2e-b4d9-afe0b7cb8f00"
},
//Example of a request for the logged in user requesting testDynamicApproval
{
"name":"testDynamicApproval",
"description":"Select this workflow if you don\u0027t have access to dyngroup2",
"label":"Gain access to dyngroup2",
"encryptedParams":"eyJpdiI6InZXOTY5QzM1WUxWNjJLeU1wVXZ6bndcdTAwM2RcdTAwM2QiLCJlbmNyeXB0ZWRSZXF1ZXN0IjoiVVdBOEF4c2FYVG9Mb1JYRXRqUTdwL2JPbUtJekdCb1lsZEppYmpzbTU5R2ZiazV3VmhwWXZtS1FwbldEZXlXRUVzY1VSUmozdVhTak9hWTBhYjdVOXRkVUdmQnJoZyt3czB1UEQ3MWdvRm4zdERvN0xlbHkxK3ZMalNoclpXSVNCUUlVT2wzS3ZuOXZmZ0xtVm52S0FvNDRIQVErNkVSeUVOUVNJakpXZlpZeE5XMmhCd01UR29GbjZ1RHVnUUNIZ3BqWmltMzAwUkJ2MXQ0c3BvdThvUDQzRytydm92L29VaUtjcFdDUjdZMG5ndE9PajNCZ1NQRWZrazRlakJWU0pJN1J0RXhsbFRQVXZzZjBzRlVmYlltd2pSNllpNnVIallUNVNLTjdQNElLaVlmcmRhelVEM2QvWHNpZHQxS0VVeURHWUhiclpEb1hIWG5jd29WZ3czdStScGFTZWh0ZDBLQWFMa1BCc1Zac2VvSnNnTnc2VXRYOGpwQzY4czIvQW1ZQ2wrelV6ZGx5czhUdW9sRFk5MXp2b1k1Y2JLbzkvNlo5VExOaWhtUm1Oa204UWJ1N1IxcVNzamMrc3d6ZiJ9",
"uuid":"3c389ed3-c85c-47fb-9deb-28370132d848"
}
]{
"request-demogroup": "success"
}Note that if a user attempts a pre-approval that they are not authorized for the approval will be left in an uncompleted state and will need to be acted on by an allowed approver.
Get Approvals
Purpose |
Retrieves the approvals for the current user |
URI |
/scale/main/approvals |
Method |
Get |
{
"approvals": [
{
"workflow": 161,
"approval": 16,
"label": "Approve Graylog Administrator",
"user": "mmosley",
"wfStart": 1458780707723,
"approvalStart": 1458780708160,
"wfName": "request-demogroup",
"wfDescription": "Demo Things",
"wfLabel": "Demo Group",
"reason": "test"
}
]
}Get Approval Details
Purpose |
Retrieves the details for a given approval |
URI |
/scale/main/approvals/APPROVALID where APPROVALID is the ID of the approval |
Method |
Get |
{
"userObj": {
"userID": "mmosley",
"groups": [
"admins",
"ipausers",
"sudoalls",
"admin-approvers",
"graylog-administrator"
],
"resync": false,
"keepExternalAttrs": false,
"JitAddToAuditDB": false,
"requestReason": "test",
"attribs": {
"Display Name": {
"values": [
"Matthew Mosley"
],
"name": "Display Name"
},
"Login ID": {
"values": [
"mmosley"
],
"name": "Login ID"
},
"First Name": {
"values": [
"Matt"
],
"name": "First Name"
},
"Last Name": {
"values": [
"Mosley"
],
"name": "Last Name"
},
"Email Address": {
"values": [
"matt.mosley@tremolosecurity-test.com"
],
"name": "Email Address"
}
}
},
"workflow": 161,
"approval": 16,
"label": "Approve Graylog Administrator",
"user": "mmosley",
"wfStart": 1458780707723,
"approvalStart": 1458780708160,
"wfName": "request-demogroup",
"wfDescription": "Demo Things",
"wfLabel": "Demo Group",
"reason": "test"
}Act on Approval Request
Purpose |
Completes an approval request |
URI |
/scale/main/approvals/APPROVALID where APPROVALID is the ID of the approval |
Method |
Put |
{
"reason": "test",
"approved": true
}List Reports for an Organization
Purpose |
Retrieves the reports for a given organizations id |
URI |
/scale/main/reports/org//ORGID where ORGID is the organization’s ID |
Method |
Get |
{
"reports": [
{
"name": "Open Approvals",
"description": "Lists all of the approvals that are currently waiting action",
"parameters": [
],
"orgID": "1c2cad5b-f62c-491c-84f3-068f6231f053"
},
{
"name": "Completed Approvals",
"description": "All approvals completed in a given set of dates",
"parameters": [
"beginDate",
"endDate"
],
"orgID": "1c2cad5b-f62c-491c-84f3-068f6231f053"
},
{
"name": "Single User Change Log",
"description": "All changes to the chosen user",
"parameters": [
"userKey"
],
"orgID": "1c2cad5b-f62c-491c-84f3-068f6231f053"
},
{
"name": "Change Log for Period",
"description": "Changes to all users between the two selected dates",
"parameters": [
"beginDate",
"endDate"
],
"orgID": "1c2cad5b-f62c-491c-84f3-068f6231f053"
}
]
}Run Report
Purpose |
Executes a report |
URI |
/scale/main/reports/REPORT_NAME?beginDate=UnixTime&endDate=UnixTime&userKey=username where REPORT_NAME is the name of the report to execute |
Method |
Get |
{
"name": "Change Log for Period",
"description": "Changes to all users between the two selected dates",
"headerFields": [
"Workflow Name",
"Request Reason",
"Workflow Started",
"Workflow Completed",
"First Name",
"Last Name",
"Email Address"
],
"dataFields": [
"Action",
"Target Type",
"Name",
"Value"
],
"grouping": [
{
"header": {
"Workflow Started": "2016-03-15 00:59:47.64",
"Request Reason": "",
"Workflow Name": "ipa-jit",
"Workflow Completed": "2016-03-15 00:59:56.0"
},
"data": [
{
"Action": "Replace",
"Value": "********************************",
"Target Type": "Attribute",
"Name": "userPassword"
}
]
},
{
"header": {
"Workflow Started": "2016-03-15 01:00:19.05",
"Request Reason": "",
"First Name": "Matt",
"Workflow Name": "ipa-jit",
"Workflow Completed": "2016-03-15 01:00:25.387",
"Last Name": "Mosley",
"Email Address": "matt.mosley@tremolosecurity-test.com"
},
"data": [
{
"Action": "Replace",
"Value": "********************************",
"Target Type": "Attribute",
"Name": "userPassword"
}
]
}
]
}ScaleJS Token
The ScaleJS Token service is helpful for getting users a token, wether thats a temporary password, TOTP or access key.
All URLs assume that scale’s filter is deployed to /scale-token.
Get Configuration
Purpose |
Retrieves the configuration for ScaleJS |
URI |
/scale-token/token/config |
Method |
Get |
{
"frontPage": {
"title": "Azure Cloud Linux Temporary Password",
"text": "Use this password for applications that do not support SSO"
},
"logoutURL": "\/logout",
"homeURL": "\/scale\/index.html"
}Get User
Purpose |
Retrieves the user and token |
URI |
/scale-token/token/user |
Method |
Get |
{
"displayName": "Matthew Mosley",
"token": {
"Temporary Password": "rgQAJvgT7vR7fiswKPLmw==:JboMmF3nQ49Sjzt0ynsN+dKB09McaIisvM3EBYivIeo="
}
}ScaleJS Single Request
This service will request the single workflow on behalf of the authenticated user calling the API.
Get Config
Purpose |
Retrieves the configuration |
URI |
/request/single-request/config |
Method |
Get |
{
"config": {
"frontPage": {
"title": "Request Access to the System Portal",
"text": "Provide the reason why you need access to the System Infrastructure Portal. Once action is taken you will be notified."
},
"logoutURL": "\/logout",
"homeURL": "\/scale\/index.html",
"uidAttribute": "adObjectGUID"
},
"displayName": "Some User"
}Post Request
Purpose |
Retrieves the configuration |
URI |
/request/single-request/submit |
Method |
Post |
{
"reason":"job responsibilities"
}Legacy Provisioning API
Introduction
Unison provides a simple api for interacting with the virtual directory and workflow engines. The API can be used to search for users or execute workflows to update or create users. The API operations are described below and rely on JSON for encapsulating requests and data. The API is authenticated using SSL mutual authentication.
The key difference between the legacy API and the new RESTful API is how the API is run. The legacy API runs as a "super user" with no controls on who can do what. This means that the application that interacts with the web services needs to keep the keystore very secure. This API offers more options at present but has more strict security requirements.
To get started you will need:
-
An HTTP api that recognizes 302 redirects and can manage cookies
-
A certificate and key that is trusted by Unison
-
The base URL for the Unison server
Most modern HTTP APIs can satisfy these requirements.
How the API Works
When using the RESTful API the sequence is:
-
Login by accessing the login service
-
HTTP GET on the user lookup API
-
HTTP POST on the workflow API
When calling the login API authentication is performed based on the certificate used to establish the SSL session. The user lookup API can look for a user based on their uid, a filter or dn. Finally, the workflow API is used to push user data into a workflow. The workflow engine is data centric, not CRUD centric. This means that the engine will perform a sync. Its recommended to use a JSON library when encoding JSON. All operations result in an implementation of the com.tremolosecurity.provisioning.service.util.ProvisioningResult class. See the SDK for specific properties on this class. If an api call is successful there will be at least one property called "success" with a value of "true". The SDK provides implementations for serializing and deserializing responses in both Java and .Net.
Reliability and Asynchronous Execution
By default all workflows executed by the api are asynchronous and "reliable". Responses are returned before the workflow is completed and if a step should fail for some reason, ie a directory or database is down, the task is retried.
Operations
Login
The login operation establishes a session for the user associated with the SSL certificate used for SSL mutual authentication to be able to interact with the API. Once this operation is complete a session cookie is generated and used moving forward.
Operation |
Login |
URI |
/services/wf/login |
HTTP Operation |
GET |
Parameters |
None |
Return |
HTTP 200;
|
User Lookup
The web services API provides a simple user lookup system for getting user attributes. This interface is not meant to replace the LDAP Virtual Directory but is meant to provide a simple way for systems interacting with Unison’s provisioning services to retrieve user information as Unison sees it. The service can only return a single user. A user can be looked up in three ways:
-
UID – Unison will look up the user based on their uid attribute
-
Distinguished Name – Searches for the user based on their distinguished name inside of Unison’s virtual directory
-
LDAP Filter – Uses an LDAP filter to search for the user
The response from the service is a JSON object that encapsulates the user with the following syntax:
{
"success":true,
"user":
{
"uid":"testsaml2",
"dn":"uid03dtestsaml2,ou03dinternal,ou03dGenericLDAP,o03dTremolo",
"directory":"GenericLDAP",
"attributes":
[
{"values":["testsaml2"],"name":"uid"},
{"values":["Boston"],"name":"l"},
{"values":["SAML2"],"name":"sn"},
{"values":["Test SAML2"],"name":"cn"},
{"values":["inetOrgPerson"],"name":"objectClass"}
],
"groups":["linkedSAMLUsers"]
}
}If no entry is found then success will be "false" and there will be no user object.
Property |
Description |
uid |
The unqiue user id mapped to the uid attribute |
dn |
The distinguished name inside of the Unison virtual directory |
attributes |
List of name/value pairs of attributes. Each attribute is a list of strings |
directory |
The name of the directory in Unison the user was found in |
groups |
List of groups the user is a member of |
Below are the options for calling the user lookup service
Operation |
User Lookup |
URI |
/services/wf/search |
HTTP Operation |
GET |
Parameters |
Search – One of: uid, dn or filter Restrict Attributes – attr for each attribute (ie attr=cn&attr=sn&attr=mail) |
Return |
HTTP 200; text/json; Described above |
Execute Workflow
Unison’s workflow engine can be utilized by applications to create users, update their attributes or reset their passwords. Workflows are not CRUD, individual target implementations are responsible for synchronizing data. There are two types of workflows:
-
Full Synchronization – All attributes are synchronized, any missing attributes or groups are removed from the user
-
Add-Only Synchronization – The attributes that are in the request are added, but missing attributes and groups are not removed
Work with your Unison administrator to build out the appropriate workflows. The request for a workflow must contain JSON encoded object that tells Unison which workflow to execute and the user data for the workflow.
The encryptedParams option is only needed for dynamic workflows.
{
"name":"test",
"uidAttributeName":"uid",
"user":
{
"attributes":
[
{"values":["testsaml5"],"name":"uid"},
{"values":["Test SAML5"],"name":"cn"},
{"values":["SAML5"],"name":"sn"},
{"values":["Boston"],"name":"l"}
],
"groups":[],
"userPassword":"mypassword"
},
"reason":"To do my job",
"requestParams":
{
"param1":"value1",
"param2":"value2"
},
"encryptedParams":"ASDFASDFAZCVXVBQDHFQRTASDTA..."
}The request has these properties:
Property |
Description |
name |
The name of the workflow to execute |
uidAttributeName |
The name of the attribute used to determine the user’s id |
user.attributes |
List of name/values pairs of attributes. Each attribute is a list of strings called "values" with a name called "name" |
user.groups |
List of groups the user is a member of |
user.userPassword |
An optional password that may be set on user accounts |
reason |
An optional reason for the request |
requestParams |
A map of names to values for arbitrary parameters to be passed to a workflow |
Below are the options for calling the user lookup service
Operation |
Execute Workflow |
URI |
/services/wf/execute |
HTTP Operation |
POST |
Parameters |
wfcall – URL Encoded JSON request |
Return |
Executed Workflows
This service will return a list of workflows that have been succesfully completed by the user specified in the "user" parameter. This is useful when listing out which workflows a user can choose from but excluding those that have already been executed.
Operation |
Login |
URI |
/services/wf/executed |
HTTP Operation |
GET |
Parameters |
user – User’s identifier, maps to the users.userKey field in the audit database |
Return |
HTTP 200;
|
Execute Approval
Use this web service to acton on an approval request for a specific workflow. This call can either be an approval or a denial of the request with an optional reason.
Operation |
Login |
URI |
/services/approvals/execute |
HTTP Operation |
GET |
Parameters |
approvalID - The id of the approval request (from List Approvals) approver - The name of the approver acting on the request, should map to the approvers.userKey field approved - true or false, if the request is approved or not reason - The reason for this response |
Return |
HTTP 200;
|
List Approvals
This service lists the open approvals for a given user. Use the output of this service when executing an approval.
{
"success":true,
"summaries":
{
"approvals":
[
{
"workflow":1,
"approval":1,
"label":"Approve Access to LDAP",
"user":"testsaml10",
"wfStart":1392512787000,
"approvalStart":1392512788000,
"wfName":"testApproval",
"wfDescription":"Select this workflow if you don",
"wfLabel":"Gain access to the portal",
"reason":"this is a test workflow webservice"
}
]
}
}{
"success": true,
"approvalDetail": {
"userObj": {
"userID": "testsaml10",
"groups": [
],
"resync": false,
"keepExternalAttrs": false,
"JitAddToAuditDB": true,
"requestReason": "this is a test workflow webservice",
"attribs": {
"uid": {
"values": [
"testsaml10"
],
"name": "uid"
},
"l": {
"values": [
"Boston"
],
"name": "l"
},
"sn": {
"values": [
"SAML5"
],
"name": "sn"
},
"cn": {
"values": [
"Test SAML5"
],
"name": "cn"
}
}
},
"workflow": 1,
"approval": 1,
"label": "Approve Access to LDAP",
"user": "testsaml10",
"wfStart": 1392513182000,
"approvalStart": 1392513182000,
"wfName": "testApproval",
"wfDescription": "Select this workflow if you dont ha",
"wfLabel": "Gain access to the portal",
"reason": "this is a test workflow webservice"
}
}Operation |
List Approvals |
URI |
/services/approvals/list |
HTTP Operation |
GET |
Parameters |
approver - The name of the approver acting on the request, should map to the approvers.userKey field approvalID - The id of the approval for a more detailed response, 0 for a list of summaries |
Return |
HTTP 200; text/json; Described above |
When settings approvalID to 0 a list of summaries for all open approval requests for the user are returned. Each summary has the following attributes:
approval |
ID of the approval |
label |
Label for the approval request |
user |
User’s name, maps to the users.userKey value |
wfStart |
Timestamp of when the workflow was initiated, as milliseconds since epoch |
approvalStart |
Timestamp of when the approval was initiated, as milliseconds since epoch |
wfName |
Name of the workflow the approval is a part of |
wfDescription |
Description of the workflow the approval is a part of |
wfLabel |
Descriptive label for the workflow the approval is a part of |
reason |
The reason for the original request |
If an approvalID is specified the above attributes are returned for a single approval request along with the details of the user the workflow is being acted upon.
List Organizations
Use this service to lookup the organizations that a user is a member of. Organizations are returned in a hierarchy.
{
"success": true,
"org": {
"id": "{123-456-7890123SDF}",
"name": "Root",
"description": "Root of all organizations",
"subOrgs": [
{
"id": "{123-456-7890123SDF}",
"name": "Org1",
"description": "First organization",
"subOrgs": [
]
},
{
"id": "{123-456-7890123SDF}",
"name": "Org2",
"description": "Second organization",
"subOrgs": [
]
}
]
}
}Operation |
List Organizations |
URI |
/services/wf/orgs |
HTTP Operation |
GET |
Parameters |
uid - User identifier uidAttr - The name of the attribute that holds the user identifier (ie uid, mail, etc) |
Return |
If no approvalID is specified - HTTP 200; |
Only organizations that the user is authorized for are returned.
List Workflows
This service lists out all available workflows. An optional uuid parameter may be specified to list the workflows for a particular organization. If a workflow is dynamic it will be returned multiple times with two additional parameters: encryptedParams for the parameters generated by the dynaic workflow implementation and uuid as a random id for this instance of the workflow. This is to make sure they do not get over-ridden by a client.
{
"success": true,
"wfDescriptions": [
{
"name": "wf1",
"label": "Application 1",
"description": "Workflow to request application1"
},
{
"name": "wf2",
"label": "Application 2",
"description": "Workflow to request application2"
},
{
"name": "wf3",
"label": "Application 3",
"description": "Workflow to request application3"
},
{
"name": "testDynamicApprovalx",
"description": "Select this workflow if you don't have access to dyngroup1",
"label": "Gain access to dyngroup1",
"encryptedParams": "eyJpdiI6Ik9WK00zYm1KdlduTmM0TEJoZmplNmdcdTAwM2RcdTAwM2QiLCJlbmNyeXB0ZWRSZXF1ZXN0IjoibEt0Ymh0TzZ0ZW9KdndKdDM3czNIYU13UEpjVTZyemxYaUVJdHI0L0JSeCtpSGk2Yk4wUmduckZ4M0VkR2Y5R2R2QW5tNExKSEtZMSs3Sk5QZTl4aTl1ckZSdE5WRU5sN2ZzcVJGdkx2Z2RYS0Q5d0lWZGIrK1hyTFJWaE5RR09Bc0h0eG92a0tJb3FOR1JGQ2ZYeUozeXl1OXVQaHdxeTRkSDJ1WDNWeUJyRVhCTnVPekJFVHM1TVlwOWFrTGZUVVIxekh2elhpZWc5TmNKcjdEenpBVEM2cFUvQ29qVkN0dHN5Si9CVFQyVjd5K2F3azRUZklKY1BiUzNxeGNqVkNpRVQyeEdPWm5hR2hKemx3Z2ZSaXgrdTJ1Y3VwSWUxdDQzQkpkRmY2OTFwK1RDSldWeDZWZHNlZmduUGlTSy9BaCtuWmJEZ1d6WGhzTkQ0ci9lcXNidDJ0N1pMOGdPU1d5TElXUDl2TXAvQXBNL0p2SW0wTUN4Q2czcERNdkVUNFJJMjFoaTNTaFptTXRQY1R5UG1BMGhlVmpGK2FIZEZQUi93RGd0bEN6dGxleTdaVXdUbVRiZXY1TGFkRlNNSSJ9",
"uuid": "52fcbc9b-cebd-4177-a903-dd6b1086afc1"
},
{
"name": "testDynamicApprovalx",
"description": "Select this workflow if you don't have access to dyngroup2",
"label": "Gain access to dyngroup2",
"encryptedParams": "eyJpdiI6Iml6bEpEejBIVVlPNU9JUEhld3hRRGdcdTAwM2RcdTAwM2QiLCJlbmNyeXB0ZWRSZXF1ZXN0IjoiQ3NjNGFsRm82bTZsOUdWWnExM0tjSFNxdlVZd0ZUTjVOQmRZVHY2dWtCZU9hMU1DVjgwL1hoNDZJYm4zZlFvVlFRUDRnWWJpRjJnbm9MV2c5RG1QMnNINGNKZEJ5alIzZ2VJUTlWNCtJaEEwVkh1T1JPbitJMGJtRTZWd0lCVlVKb0tOWlR3TFhRU3dtQzl0WmN1VldjeGw2anBPK1ZidTBOOGpEUzVLSFZKQzJNc0RoSytRSVhEVHFtT1NGLzh0aHlSYitLTkk4d0Y4Mjg2blhNSyszREsyaElaT29OeVFCMnVubHExb2N1c0MxY0VrUEgycnNBSUE5TFU0ak5RaTNHWW5mbzJwMlJZR0ZHUXJBdVE2VUpMSHNVTEUvcGUyL0RKWFpwVnJlY2F1dzFsMlkrYUdUdzJ2WkcvaHRSNmVRNWJlWkp6aFVSNUJpd1ZEa1RBU21oTlZGZGZCRHZPR0FhUHdtLzcxTytGUW9PZFdDUk04b05tV2ZIaGtZRE8wZk15Z3hpT1I3U3N3Rk9Sdkxrak1aTTBUcTR4enR2Rnd1RzNmaG5MR0tkWmZjOEF3OStuZnF0RWRmVnJkdXNLeCJ9",
"uuid": "d4a86acf-bade-4198-9b77-9cf9755a53b4"
}
]
}Operation |
List Workflows |
URI |
/services/wf/list |
HTTP Operation |
GET |
Parameters |
uuid - Optional: id of organization to limit returned workflows from |
Return |
HTTP 200; |
List Portal URLs
The List Portal URLs service is used in conjunction with the Portal URLs management screen in Unison to provide a list of links of a user’s authorized applications. This API is self contained, all icons for links are provided as Base64 encoded PNG files. These images can be displayed in a browser using the "data" method of an img tag:
<img height="240" width="210" src"data:image/png;base64,..." />Where the "…" is the base64 encoding of the image file returned by this web service.
Operation |
List Portal URLs |
URI |
/services/portal/urls |
HTTP Operation |
GET |
Parameters |
|
Return |